As I mentioned in my previous post, I am currently working on enabling Single Sign On (SSO) for my Salesforce Org. To do this research, I needed an identify provider that would act as my SAML end point to validate identity requests and respond with valid SAML responses. Well I figured why dont i setup another one of my Salesforce orgs as an Idp provider.
Below are the steps i followed to enable one of my Salesforce Orgs as an Idp that is capable of sending SAML responses to valid requests -
- As a prerequisite to enabling an org as an Idp, you will need to setup a My Domain for that environment. Please see my previous blog for instructions - Setup my Domain on Salesforce.
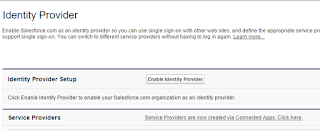
- For the org that will act as your Identity Provider, navigate to the Setup -> Security Controls -> Identity Providers screen
- Now click the Enable Identity Provider button
- In the next step, you will be asked to select a certificate to enable secure communication of the SAML requests and responses. You can choose the Salesforce provided self-signed certificate or use another certificate that you may have already imported into the "Certificates and Key Management" screen previously. Since this is just a research setup on my developer edition org, i am going to use the Salesforce provided certificate.
- Thats it, your org is now enabled to act as an Idp with ability to respond to SAML requests. The resulting screen will show as below -
- It has the SAML endpoint details and has a button that enables you to download all metadata needed at the service provider side to enable SSO
- As a next step you will need to add your Service Provider as a Connected app in this org. Since in my experiment I am adding another Salesforce org as my service provider (to enable it for SSO), i will add that in a separate post. Update - I added the steps for adding the connected app in the above Salesforce app in following post - Setting up an SSO enabled connected app.
.


Comments
Post a Comment